SQL injection is a type of security vulnerability that occurs when an attacker is able to insert or "inject" arbitrary SQL code into a query. This typically happens due to insufficient validation or sanitization of user input within an application that interacts with a database. SQL injection can leRead more
SQL injection is a type of security vulnerability that occurs when an attacker is able to insert or “inject” arbitrary SQL code into a query. This typically happens due to insufficient validation or sanitization of user input within an application that interacts with a database. SQL injection can lead to unauthorized access to or manipulation of the database, allowing attackers to view, modify, or delete data.
Here’s a basic example to illustrate how an SQL injection might work:
- Vulnerable SQL Query:
In this query,
userandpassare placeholders for user-provided input. - Injection Attack: Suppose the application constructs the SQL query by concatenating strings directly with user inputs:
An attacker could input
userInputUsernameasadmin' --and leave the password field empty. This might result in the following query:This might allow the attacker to log in as the admin user without providing a password.
Common Types of SQL Injection:
- Classic SQL Injection: The basic form where attackers manipulate query strings.
- Blind SQL Injection: When the attacker cannot see the direct results of their injection but can infer information based on the application’s behavior.
- Error-based SQL Injection: Exploiting database errors to gain information about the structure of the database.
- Union-based SQL Injection: Using the
UNIONSQL operator to combine results from two or moreSELECTstatements.
Prevention Methods:
- Parameterized Queries (Prepared Statements): Ensure user input is treated as data, not code.
- Stored Procedures: Encapsulate SQL logic within the database to reduce the risk.
- Input Validation and Sanitization: Validate and sanitize all user inputs to ensure they meet expected patterns.
- Use of ORMs (Object-Relational Mappers): These tools can help manage database access more safely.
- Least Privilege Principle: Ensure that database accounts have the minimum necessary permissions.
By following these practices, developers can significantly reduce the risk of SQL injection attacks.
See less
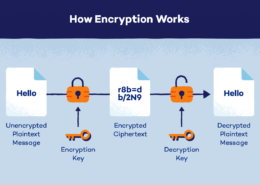
SQL injection is a type of web application security vulnerability that allows an attacker to inject malicious SQL code into a web application's database in order to extract or modify sensitive data. This is typically done by inserting malicious input into a web form or URL, which is then processed bRead more
SQL injection is a type of web application security vulnerability that allows an attacker to inject malicious SQL code into a web application’s database in order to extract or modify sensitive data. This is typically done by inserting malicious input into a web form or URL, which is then processed by the application’s database.
See lessWhen a web application uses user-input data to construct SQL queries, an attacker can inject malicious SQL code as part of the input. If the application does not properly sanitize or validate the input, the malicious code can be executed by the database, allowing the attacker to access or modify sensitive data.
SQL injection attacks can be used to extract sensitive data, such as passwords or credit card numbers, or to modify data, such as inserting or deleting records. In some cases, an attacker may even be able to gain administrative access to the database or entire system.
SQL injection attacks can be prevented by using prepared statements, input validation, and escaping special characters to ensure that user-input data is not executed as SQL code. Regular security testing and code reviews can also help identify and fix vulnerabilities before they can be exploited.