Blockchain technology's decentralized nature is revolutionizing cybersecurity in several key ways: 1. Distributed Ledger: Blockchain operates as a distributed ledger, meaning that data is stored across a network of computers (nodes) rather than a single central server. This makes it much moreRead more
Blockchain technology’s decentralized nature is revolutionizing cybersecurity in several key ways:
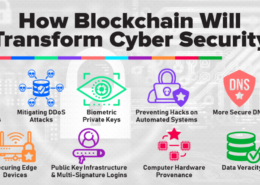
1. Distributed Ledger: Blockchain operates as a distributed ledger, meaning that data is stored across a network of computers (nodes) rather than a single central server. This makes it much more difficult for hackers to attack because there is no single point of failure. Compromising the network would require simultaneously attacking a majority of the nodes.
2. Immutability: Once data is recorded on a blockchain, it is extremely difficult to alter. This immutability helps prevent unauthorized changes and tampering. Each block is cryptographically linked to the previous one, creating a secure chain of information.
3. Transparency and Traceability: Transactions on a blockchain are transparent and can be traced back to their origin. This transparency deters fraudulent activities and enhances trust, as all participants can see the same information and verify it independently.
4. Decentralized Consensus: Blockchain uses consensus mechanisms (such as Proof of Work or Proof of Stake) to validate transactions. This means that no single entity controls the verification process, reducing the risk of corruption or manipulation.
5. Enhanced Security Protocols: Blockchain technology employs advanced cryptographic techniques to secure data. Public and private keys, along with digital signatures, ensure that only authorized users can access and execute transactions.
6. Smart Contracts: These are self-executing contracts with the terms directly written into code. They automatically enforce and execute agreements when predetermined conditions are met, reducing the need for intermediaries and enhancing security through automation.
By decentralizing data storage and verification, blockchain technology significantly enhances cybersecurity, making systems more resilient to attacks, reducing fraud, and increasing trust among users.
See less
Balancing robust cybersecurity with digital transformation and productivity requires a strategic approach. Organizations can achieve this by adopting a risk-based security model, prioritizing measures based on the specific threats they face. Integrating security into the development lifecycle througRead more
Balancing robust cybersecurity with digital transformation and productivity requires a strategic approach. Organizations can achieve this by adopting a risk-based security model, prioritizing measures based on the specific threats they face. Integrating security into the development lifecycle through DevSecOps ensures vulnerabilities are addressed early, minimizing disruptions. Implementing user-friendly security solutions that do not hinder productivity can also foster compliance.
Key challenges include resource allocation, employee resistance, integration complexity, evolving threats, regulatory compliance, and skill gaps. Addressing these involves several strategies:
By embedding security into the core of digital initiatives and maintaining a proactive stance, organizations can enhance both security and productivity.
See less