Home/Internal Security/Cyber Security/Page 22
Cyber Security
Share
506 Followers
862 Answers
462 Questions
Resources & Suggestions
Mains Answer Writing Latest Articles
On: April 18, 2025
Daily Answer Writing Practice Questions (18 April 2025)
Do you agree with the claim that indecision and risk aversion are prevalent issues in Indian bureaucracy? Support your answer with logical reasoning. (150 words) ऐसा कहा जाता है कि भारतीय नौकरशाही में अनिर्णय और जोखिम से बचने की प्रवृत्ति ...
On: April 18, 2025
Comments:
0
Strengthening India’s Cyber Defence
Rising Threats Digital Era Challenges: 2024 marks a significant rise in digital threats, particularly from AI and cyberattacks. Key Issues: Disinformation campaigns. Cyber fraud affecting daily life. Current Major Cyber Threats Ransomware Rampage: Over 48,000 instances of WannaCry ransomware detected ...
On: April 18, 2025
Comments:
0
भारत की साइबर सुरक्षा
बढ़ते खतरे कृत्रिम बुद्धिमत्ता (AI) और साइबर हमले: 2024 में AI और साइबर हमलों के खतरे में वृद्धि। महत्वपूर्ण अवसंरचना पर हमले: डिजिटल हमलों और दुष्प्रचार अभियानों की संभावना बढ़ी है। प्रमुख साइबर खतरें रैनसमवेयर का प्रकोप: 48,000 से अधिक ...

How does the OSI model facilitate network communication?
The OSI (Open Systems Interconnection) model facilitates network communication by providing a standardized framework that divides network communication into seven distinct layers. Each layer has specific functions and protocols that contribute to the overall process of transmitting data between deviRead more
The OSI (Open Systems Interconnection) model facilitates network communication by providing a standardized framework that divides network communication into seven distinct layers. Each layer has specific functions and protocols that contribute to the overall process of transmitting data between devices.
By segmenting communication into these layers, the OSI model standardizes network functions, promoting interoperability and simplifying troubleshooting and development.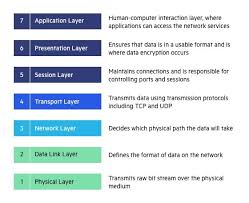
See lessHow does encryption work, and why is it essential for securing data and communications?
Encryption is the transformation of plaintext data into ciphertext (encrypted text), which means the destruction of its structure in such a way that without the appropriate decryption key, it is impossible to read the information. The two main types of Encryptions: Symmetric Asymmetric Symmetric encRead more
Encryption is the transformation of plaintext data into ciphertext (encrypted text), which means the destruction of its structure in such a way that without the appropriate decryption key, it is impossible to read the information.
The two main types of Encryptions:
Symmetric encryption means use of one key, intended for both encryption and decryption. It’s faster since only receiver side must have a key, but there is a need to maintain the security of key.
Asymmetric encryption is distinguished by the presence of two keys – a public key and private secret key for encryption and decryption, respectively. In this way, a user can share a public key with anyone without sending a secret one.
The strength of the encryption lies in complexity of algorithms and key length such that it becomes computationally impossible to decrypt the plaintext without use of a key if the entity is unauthorized. Hence, encryption plays a big role in securing data and communication as it provides confidentiality, integrity, and authentication. It protects sensitive information against unauthorized access while it is being stored or transmitted and secures online transactions from data breaches. With the ever-increasing cyber-attacks, encryption is the backbone of digital communications concerning privacy and trust.
See lessWhat role does user awareness and training play in preventing cybersecurity incidents?
User awareness and training are crucial in preventing cybersecurity incidents by: 1. Identifying phishing attacks: Training helps users recognize suspicious emails and avoid malicious links. 2. Safe browsing practices: Users learn to avoid malicious websites and understand the importance of HTTPS. 3Read more
User awareness and training are crucial in preventing cybersecurity incidents by:
1. Identifying phishing attacks: Training helps users recognize suspicious emails and avoid malicious links.
See less2. Safe browsing practices: Users learn to avoid malicious websites and understand the importance of HTTPS.
3. Password security: Emphasizes creating strong, unique passwords and not reusing them.
4. Recognizing social engineering: Teaches users to identify and verify manipulative tactics used by attackers.
5. Data handling: Educates users on protecting sensitive information and preventing data leaks.
6. Incident reporting: Encourages prompt reporting of suspicious activities and understanding proper procedures.
7. Device security: Covers securing personal devices and safe use of public Wi-Fi.
8. Remote work best practices: Emphasizes secure remote access methods and avoiding risks associated with public networks.
9. Regular updates and patching: Stresses the importance of keeping software updated to protect against vulnerabilities.
10. Creating a security culture: Encourages continuous vigilance and proactive security measures through regular training and reminders.
How does cybersecurity relate to compliance with regulations such as GDPR, HIPAA, and PCI-DSS?
Cybersecurity is essential for compliance with regulations like GDPR, HIPAA, and PCI-DSS, which are designed to protect sensitive information. GDPR (General Data Protection Regulation): This European regulation requires organizations to protect personal data and ensure privacy. Cybersecurity measureRead more
Cybersecurity is essential for compliance with regulations like GDPR, HIPAA, and PCI-DSS, which are designed to protect sensitive information.
Key Points:
By prioritizing cybersecurity, organizations can achieve compliance with regulations like GDPR, HIPAA, and PCI-DSS, thereby protecting sensitive data and maintaining trust with their stakeholders.
See lessAccess Management
To build a robust Identity and Access Management (IAM) system, consider these key elements: Centralized Identity Management: Use a single system to manage user identities, ensuring consistency and security across the organization. Role-Based Access Control (RBAC): Assign permissions based on roles rRead more
To build a robust Identity and Access Management (IAM) system, consider these key elements:
In a multi-cloud environment, managing identities and access rights can be challenging. Here are some strategies:
To implement MFA effectively without disrupting user experience:
By integrating these elements and strategies, organizations can manage user identities and access rights effectively while ensuring a smooth user experience.
See lessWhat are the ethical considerations surrounding cybersecurity, particularly in terms of privacy and data protection?
Cybersecurity involves protecting computers, networks, and data from unauthorized access or damage. Ethical considerations in cybersecurity, especially regarding privacy and data protection, are crucial. Firstly, respecting privacy means safeguarding personal information stored online, such as namesRead more
Cybersecurity involves protecting computers, networks, and data from unauthorized access or damage. Ethical considerations in cybersecurity, especially regarding privacy and data protection, are crucial.
Firstly, respecting privacy means safeguarding personal information stored online, such as names, addresses, and passwords. Ethical cybersecurity practices ensure this data isn’t accessed or used without permission, preventing identity theft or fraud.
Secondly, data protection involves securing sensitive information, like medical records or financial details, against theft or manipulation. Ethical hackers (also known as white hat hackers) play a role here by testing systems to find vulnerabilities and fix them before malicious hackers can exploit them.
Ethics also guide how companies handle data breaches. Promptly informing affected individuals and taking steps to mitigate harm demonstrates accountability and trustworthiness.
School students can think of cybersecurity ethics like being a good digital citizen: respecting others’ privacy, being honest in online interactions, and using technology responsibly. By understanding and practicing ethical cybersecurity, we contribute to a safer and more trustworthy digital world for everyone.
See lessWith digital learning becoming the norm, how can educators effectively integrate cybersecurity awareness into curriculums to empower students to navigate the online world safely?
In today's digital age, integrating cybersecurity awareness into educational curriculums is crucial to empower students to navigate the online world safely. Educators can effectively achieve this by embedding cybersecurity principles across various subjects and activities. Firstly, incorporating dedRead more
In today’s digital age, integrating cybersecurity awareness into educational curriculums is crucial to empower students to navigate the online world safely. Educators can effectively achieve this by embedding cybersecurity principles across various subjects and activities.
Firstly, incorporating dedicated cybersecurity modules or lessons within IT and computer science courses helps students grasp fundamental concepts such as data protection, password security, and safe internet browsing. These lessons should be practical, involving hands-on activities like creating strong passwords or identifying phishing emails to engage students actively.
Moreover, integrating cybersecurity discussions into broader subjects like social studies or ethics can foster critical thinking about online behaviors and digital citizenship. This approach encourages students to understand the ethical implications of their online actions and the importance of respecting digital privacy.
Additionally, schools can organize workshops, guest lectures from cybersecurity experts, or cybersecurity-themed events to expose students to real-world scenarios and practical advice. Collaborations with industry partners can provide insights into current cybersecurity trends and career opportunities in the field.
By embedding cybersecurity awareness throughout the curriculum, educators not only equip students with essential digital skills but also cultivate a proactive mindset towards cybersecurity, preparing them to navigate the online world safely and responsibly.
See lessBeyond awareness campaigns, what concrete steps are Indian businesses taking to train their employees in recognizing and defending against cyberattacks?
Indian businesses are increasingly recognizing the importance of training their employees to recognize and defend against cyberattacks. Beyond awareness campaigns, here are some concrete steps they are taking: 1. Structured Training Programs Regular Cybersecurity Training: Many organizations are insRead more
Indian businesses are increasingly recognizing the importance of training their employees to recognize and defend against cyberattacks. Beyond awareness campaigns, here are some concrete steps they are taking:
1. Structured Training Programs
2. Simulation Exercises and Drills
3. Certification and Professional Development
4. Advanced Security Workshops
5. Gamification of Cybersecurity Training
6. Onboarding Training
7. Security Awareness Programs
8. Security Policies and Guidelines
9. Use of Security Tools and Platforms
10. Creating a Cybersecurity Culture
By adopting these strategies, Indian businesses are enhancing their employees’ ability to recognize and defend against cyberattacks, thereby strengthening their overall cybersecurity posture.
See lessHow far India's digital infrastructure is developed to tackle cyber attacks like ransomware and others. What are new steps that can be taken? are
India's digital infrastructure has seen significant development over recent years, but tackling sophisticated cyber threats like ransomware still requires continuous enhancement and proactive measures. Here’s an overview of the current state and steps that can be taken to improve resilience againstRead more
India’s digital infrastructure has seen significant development over recent years, but tackling sophisticated cyber threats like ransomware still requires continuous enhancement and proactive measures. Here’s an overview of the current state and steps that can be taken to improve resilience against cyber attacks:
Current State of India’s Digital Infrastructure
Areas for Improvement and New Steps
By implementing these steps, India can significantly bolster its digital infrastructure to better withstand cyber attacks like ransomware and ensure a more secure digital environment for its citizens and businesses.
See lessEthical Challenges in Implementing Transparent Data Practices
Transparent data practices, where users understand how their information is collected and used, are crucial in today's data-driven world. However, implementing them ethically presents several challenges: Balancing Transparency with Privacy: Data Security: Increased transparency can expose data, makiRead more
Transparent data practices, where users understand how their information is collected and used, are crucial in today’s data-driven world. However, implementing them ethically presents several challenges:
Balancing Transparency with Privacy:
User Comprehension and Control:
Algorithmic Bias and Fairness:
Additional Challenges:
Conclusion:
Transparent data practices are a worthy goal, but ethical considerations require careful navigation. By addressing these challenges, organizations can build trust with users and ensure responsible data collection and utilization.