8.How does literature reflect and shape cultural and societal values across different historical periods?
Mains Answer Writing Latest Questions
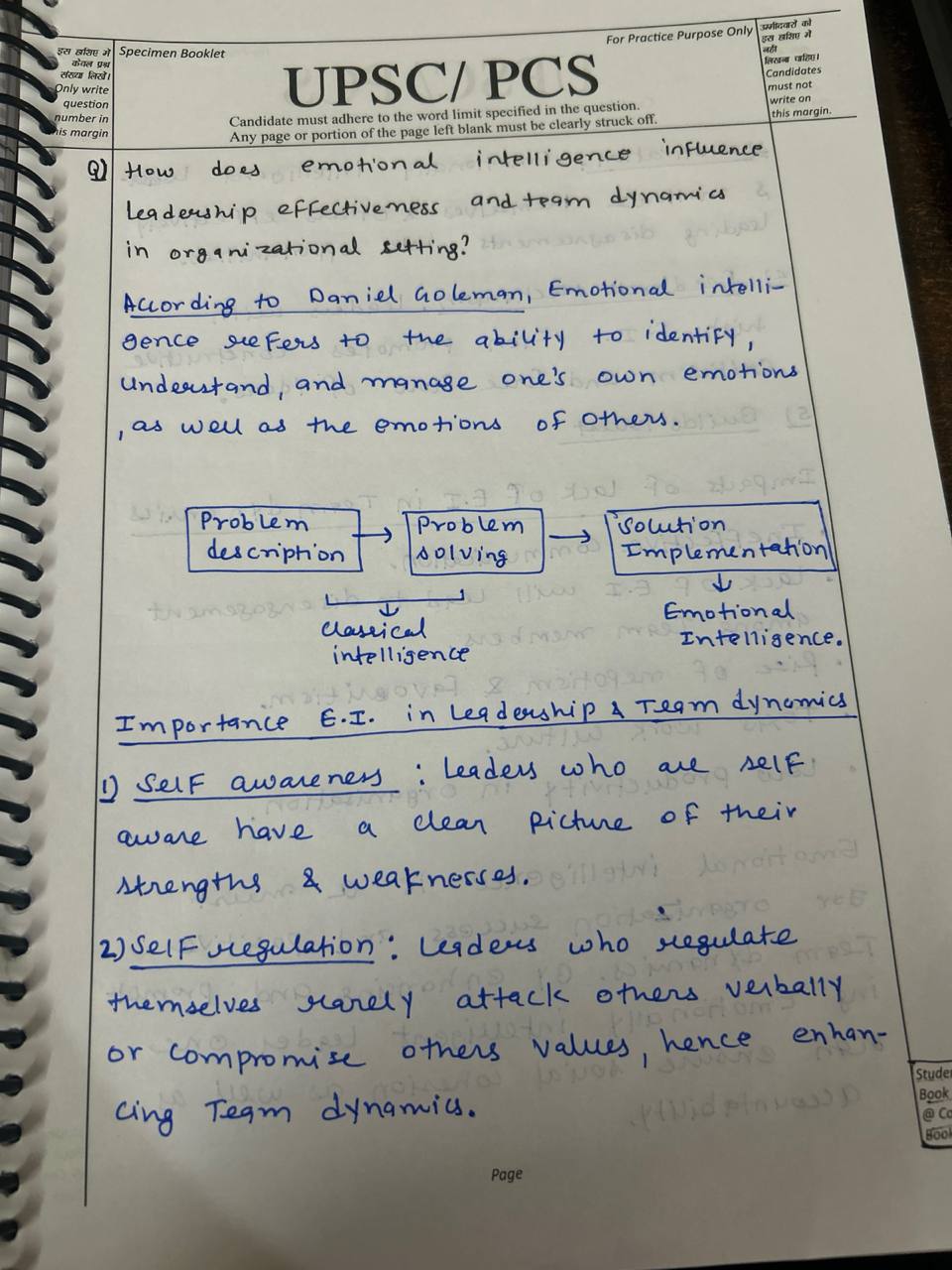
6.How does emotional intelligence influence leadership effectiveness and team dynamics in organizational settings?
5.What are the psychological and social mechanisms through which attitudes are formed, changed, and maintained?
How can educational institutions balance the integration of technology with traditional teaching methods to optimize learning outcomes?
-
Balancing technology with traditional teaching methods involves several strategies: Hybrid Learning Models: Implement a blend of online and face-to-face instruction. This can include using digital tools for homework, assessments, and collaborative projects while maintaining classroom-based discussioRead more
Balancing technology with traditional teaching methods involves several strategies:
- Hybrid Learning Models: Implement a blend of online and face-to-face instruction. This can include using digital tools for homework, assessments, and collaborative projects while maintaining classroom-based discussions and activities.
- Tailored Integration: Use technology where it complements traditional methods. For example, interactive simulations can enhance understanding of complex concepts, while direct instruction can address foundational knowledge.
- Professional Development: Train educators to effectively integrate technology with traditional methods. This includes understanding when to use digital tools and how to incorporate them into existing curricula.
- Student-Centered Approaches: Utilize technology to cater to diverse learning styles. For instance, visual and auditory tools can support different learners, while traditional methods can be used for hands-on practice.
- Assessment and Feedback: Use technology to provide timely feedback and assess student progress, but ensure that traditional methods like in-class discussions and peer reviews are also used to gauge understanding.
- Tech Evaluation: Regularly assess the effectiveness of technological tools in achieving learning outcomes and adjust strategies accordingly.
- Infrastructure and Support: Ensure that both students and teachers have access to necessary technology and support to use it effectively alongside traditional methods.
By thoughtfully combining these approaches, educational institutions can enhance learning experiences and outcomes.
See less
4.How is climate change reshaping global geographic boundaries and impacting regional geopolitical stability?
-
Climate Change, and Its Effects on Global Geopolitical Landscape From the slower of hurricanes to the melting of the ice caps and the burning of forests, climate change is not just changing the Earth and its climate but also its geography. These shifts have profound consequences for global geographiRead more
Climate Change, and Its Effects on Global Geopolitical Landscape
From the slower of hurricanes to the melting of the ice caps and the burning of forests, climate change is not just changing the Earth and its climate but also its geography. These shifts have profound consequences for global geographic boundaries and regional geopolitical stability. But as temperatures rise, sea levels rise and weather patterns become more extreme, the world’s nations are confronting new challenges that risk redrawing borders and altering relations between countries.
Increasing Sea Levels and Coastal Erosion
Sea level rise is one of the most immediate and visible impacts of climate change. Global sea level increased by approximately 15-25 cm since 1900 and this trend will continue, according to the Intergovernmental Panel on Climate Change (IPCC). Sea levels rising threaten low-lying coastal areas, increasing coastal erosion and land loss. One of the most vulnerable spots on the globe is small island nations, including Maldives, Tuvalu, and the Marshall Islands. These islands’ potential disappearance would displace entire populations and pose questions of sovereignty and territorial integrity.
Melting Ice Caps and Sovereignty in the Arctic
Melting polar ice caps are creating new shipping routes and giving access to previously unreachable natural resources, especially in the Arctic. The trend is being seen along narrow routes formerly mostly blocked by ice: The Northwest Passage and the Northern Sea Route are increasingly viable alternatives to established shipping lanes. It has ushered in an era of new competition among Arctic nations, including Russia, Canada and the United States, for control of those routes and the resources they could unlock — oil, gas and minerals. As these resources become more available, it is expected the geopolitical tensions in the Arctic region are set to continue.
Conflicts over access to scarce water resources
Climate change is intensifying water scarcity across many regions, particularly in arid and semi-arid parts of the world. Less rainfall and more evaporation because of higher temperatures are draining water resources, triggering disputes over the use of water. The Middle East, North Africa, and the western half of South Asia are especially at risk. The Nile River basin, for example, which is co-owned by 11 countries, is one such potential flash point for conflict, as upstream countries like Ethiopia undertake large-scale hydroelectric projects that would reduce water flow downstream to nations like Egypt and Sudan.
Changes from AgrarianCroppers to OtherSpaceAgricultural Croppers
Increasing temperatures, changes in precipitation patterns, and extreme weather events are affecting agricultural productivity, with impacts on crop yields and food production. Some areas might become more suitable for agriculture, while others might become less viable.” For example, the United States and Canada’s breadbasket could change and parts of Africa and South Asia could see drastic declines in agricultural productivity. Such shifts can cause food shortages, higher food prices and social unrest, especially in areas that are already food insecure.
Border Security and Human Migration
Climate change is also already rendering some areas of the world uninhabitable and so millions could be forced to move, bringing with its own substantial demographic shift, let alone how that is handled on the border security front. The United Nations estimates that by 2050 there will be up to 1 billion climate refugees. These migrations can put the strain on the resources and social fabric of host countries, resulting in tensions and conflicts. As an example of the challenges ahead, Europe has received millions of refugees from climate change-impacted regions in response to recent climate-induced disasters and conflicts.
Natural Disasters & State Resilience
As a result of climate change, hurricanes, floods, and wildfires are becoming more frequent and intense. These events can overwhelm the response capabilities of states, which can lead to political instability and even the collapse of the state. The Haiti Earthquake of 2010 and the Typhoon Haiyan of 2013 in the Philippines are good examples of how susceptible a state will be in the wake of natural disasters, which can add fuel to the fire of pre-existing social and economic difficulties.
Global Cooperation and Climate Diplomacy
Climate change is a global phenomenon and impacts need to be addressed globally. Climate diplomacy has emerged, as countries join hands to curb greenhouse gas emissions and adapt to climate change. For example, the Paris Agreement, which was signed in 2015, is a landmark initiative in global cooperation however its implementation hinges on the actions and dedication of each and every country. A lack of adherence to this commitments may escalate geo-political tensions and instability.
Conclusion
Climate change is not simply an environmental issue. It is a geopolitical one. The physical space of the planet is undergoing its own transformation, and that has implications for international relations.) The very real threats of rising sea levels, melting ice caps, water scarcity, agricultural fathering, human migration and natural disasters are transforming the global order. The international community will need to work together more than ever to mitigate the effects of climate change and to build a world that is more environmentally sustainable and stable.
See less
3.How does corruption undermine economic development and social progress in affected regions?
Drowsiness or fatigue Dizziness or lightheadedness Nausea or vomiting Blurred vision or double vision Unsteadiness or balance issues Weight gain or loss Skin rash Mood changes or irritability It’s important to consult a healthcare provider if experiencing any side effects, as they can vary depending on the specific ...
How can emerging technologies like quantum computing impact current cybersecurity practices?
-
Quantum computing, a groundbreaking technology that exploits the principles of quantum mechanics, has the potential to take many industries by storm, including cyber security. The full effect of quantum computing is yet to be seen, but its influence over contemporary cybersecurity will be deep and fRead more
Quantum computing, a groundbreaking technology that exploits the principles of quantum mechanics, has the potential to take many industries by storm, including cyber security. The full effect of quantum computing is yet to be seen, but its influence over contemporary cybersecurity will be deep and far-reaching. In this piece we take a look at how quantum computing might undermine current security mechanisms and how best to prepare for this impending technological evolution.
Introduction to Quantum Computing
Quantum Computing Process Quantum computing is a kind of computation that uses quantum-mechanical phenomena, such as superposition and entanglement to perform operations on data. Qubits, unlike classical bits that can only be either in the state 0 or 1, can be in multiple states at a time, a feature called superposition. Qubits can also be entangled, meaning the state of one qubit can instantaneously influence the state of another, no matter how far apart they are. These features make quantum computers capable of executing particular calculations exponentially faster than classical computers.
Quantum Computing: The Transition of Cryptography
Cryptography is one of the areas of cyber security where quantum computing shows the most potential for disruption. Most modern cryptographic systems, for instance, those which involve secure communications and data protection, depend as a source of security on the computational difficulty of certain mathematical problems (e.g., the factoring of large numbers (RSA) or the discrete logarithm problem(Diffie-Hellman)). Algorithms, such as Shor’s algorithm, enable quantum computers to solve these problems much more efficiently than classical computers, putting numerous established encryption methods at risk of becoming obsolete.
Public key cryptography: Public key cryptography, the foundation of secure online transactions and communications, may be severely undermined. This means that large numbers can be factorized in polynomial time using Shor’s algorithm, and would allow large RSA encryption keys to be broken much faster than it is currently possible to do.
Symmetric Key Cryptography: Symmetric key algorithms such as AES are not as susceptible to quantum attacks as public key algorithms, but quantum computers may still significantly cut the time needed to brute force such keys, requiring longer key lengths to remain secure.
New Security Paradigms
Quantum computing’s threat to existing encryption systems has also inspired new approaches toward security:
Post- Quantum Cryptography (PQC): PQC is the designing of the cryptographic algorithms that are secure against quantum attack. This means that the algorithms should be secure even against quantum computers, and they are being researched and standardized by the likes of the National Institute of Standards and Technology (NIST).
QKD (qc=fic) Quantum Key Distribution: QKD is a technique that uses quantum mechanics principles to securely share cryptographic keys. It uses the entanglement phenomenon and allows to detect any attempt of eavesdropping, providing the secure transfer of keys. As a result, this technology is able to offer a superior degree of security and is especially beneficial for extremely confidential communications.
Preparing for Quantum Computing and Cyber Threats
Quantum computing also brings new kinds of cyber attacks:
Quantum Hackers: At some point, quantum computers will be inexpensive enough that malicious actors can use them to breach secure systems. These include decrypting sensitive data, cracking passwords and launching sophisticated attacks on critical infrastructure.
Quantum Computing: Hackers may begin harvesting encrypted data — with the hope to decrypt it in the future when quantum computers become more advanced. This long-game threat highlights the urgency of preparing for quantum-resistant security precautions today.
Preparing for the Quantum Era
Groups and organizations as well as governments need to take proactive measures to prepare for the quantum age:
Transition to PQC Algorithms: Move to post-quantum cryptographic algorithms under standardization. This involves updating protocols, systems, and applications, so that they can make use of these new algorithms.
Combine both classical and post-quantum methods into hybrid cryptographic approaches. It gives time to move towards systems that are completely resistant to quantum attacks.
Quantum-Resistant Protocols: Develop and deploy quantum-resistant communication protocols to protect against data harvesting and other quantum threats.
Investment in education and training: Ensuring that security professionals and developers are equipped with knowledge of quantum computing and its potential impact on cybersecurity.
Develop R&D: invest in the research of new cryptographic techniques and in the study of solutions to the risks involved by quantum computing
Conclusion
Quantum computing is a radical shift in tech with the potential to change the face of cybersecurity forever. The direct threat is still fairly minimal, but the potential for massive disruption is genuine. “With the emergence of quantum computers on the horizon, organizations must take the necessary measures now to secure their systems in the quantum world. By leveraging post-quantum cryptography, seeking out quantum key distribution, and taking actionable steps to prepare for the quantum age, organizations can protect against the new risks associated with burgeoning quantum computing capabilities.” Migration to quantum-secure security solutions isn’t merely a tech issues but unuiquely a optimal strategy to protect our identity and data in a digital era.
See less


Literature has long served as both a mirror reflecting societal values and a powerful force shaping cultural norms across different historical periods. As a reflection of society, literature captures the prevailing attitudes, beliefs, and concerns of its time, offering valuable insights into the humRead more
Literature has long served as both a mirror reflecting societal values and a powerful force shaping cultural norms across different historical periods. As a reflection of society, literature captures the prevailing attitudes, beliefs, and concerns of its time, offering valuable insights into the human experience within specific historical contexts. For instance, Victorian literature often explored themes of morality and social class, reflecting the rigid societal structures of 19th century England.
Simultaneously, literature has the power to challenge existing norms and introduce new ideas, thereby influencing cultural values. Works like George Orwell’s “1984” or Margaret Atwood’s “The Handmaid’s Tale” have sparked conversations about government control and women’s rights, respectively, shaping public discourse and societal attitudes.
Throughout history, literature has played a crucial role in promoting social change, from abolitionist novels like “Uncle Tom’s Cabin” to feminist works like “The Yellow Wallpaper.” By presenting alternative perspectives and highlighting societal issues, literature encourages readers to question established norms and consider new viewpoints.
Moreover, literature preserves cultural heritage, passing down traditions, myths, and values from one generation to the next. This continuity allows societies to maintain a sense of identity while also evolving with changing times. In essence, literature serves as a dynamic interplay between reflection and influence, continuously shaping and being shaped by the cultures and societies it represents.
See less