Ivan Fernandes
BegginerResources & Suggestions
Mains Answer Writing Latest Articles
Daily Answer Writing Practice Questions (18 April 2025)
Do you agree with the claim that indecision and risk aversion are prevalent issues in Indian bureaucracy? Support your answer with logical reasoning. (150 words) ऐसा कहा जाता है कि भारतीय नौकरशाही में अनिर्णय और जोखिम से बचने की प्रवृत्ति ...
Strengthening India’s Cyber Defence
Rising Threats Digital Era Challenges: 2024 marks a significant rise in digital threats, particularly from AI and cyberattacks. Key Issues: Disinformation campaigns. Cyber fraud affecting daily life. Current Major Cyber Threats Ransomware Rampage: Over 48,000 instances of WannaCry ransomware detected ...
भारत की साइबर सुरक्षा
बढ़ते खतरे कृत्रिम बुद्धिमत्ता (AI) और साइबर हमले: 2024 में AI और साइबर हमलों के खतरे में वृद्धि। महत्वपूर्ण अवसंरचना पर हमले: डिजिटल हमलों और दुष्प्रचार अभियानों की संभावना बढ़ी है। प्रमुख साइबर खतरें रैनसमवेयर का प्रकोप: 48,000 से अधिक ...

How can organizations conduct effective vulnerability assessments and penetration testing to enhance their cybersecurity defenses?
Organizations can enhance their cybersecurity defenses through effective vulnerability assessments and penetration testing by following a structured approach. Firstly, they should define clear objectives, identifying critical assets, systems, and data that need protection. Regular vulnerability asseRead more
Organizations can enhance their cybersecurity defenses through effective vulnerability assessments and penetration testing by following a structured approach.
Firstly, they should define clear objectives, identifying critical assets, systems, and data that need protection. Regular vulnerability assessments should be conducted using automated tools to scan for known vulnerabilities across the network, applications, and systems. This process should include up-to-date vulnerability databases to ensure comprehensive detection.
Next, penetration testing should be performed by skilled professionals who simulate real-world attacks to identify exploitable vulnerabilities. This involves both internal and external tests, mimicking insider threats and external attackers, respectively. Pen testers use various techniques, such as social engineering, to uncover security weaknesses.
Organizations should adopt a risk-based approach, prioritizing vulnerabilities based on their potential impact and likelihood of exploitation. The findings from assessments and tests should be documented in detailed reports, highlighting vulnerabilities, potential impacts, and recommended remediation steps.
Collaboration between security teams and other departments is crucial to address identified issues promptly. Regular follow-up assessments and tests should be conducted to ensure vulnerabilities are effectively mitigated and to adapt to the evolving threat landscape.
Additionally, fostering a culture of continuous security awareness and training for employees helps in identifying and mitigating threats early, further strengthening the organization’s cybersecurity posture.
See lessHow does the OSI model facilitate network communication?
The OSI (Open Systems Interconnection) model facilitates network communication by providing a standardized framework that divides network communication into seven distinct layers. Each layer has specific functions and protocols that contribute to the overall process of transmitting data between deviRead more
The OSI (Open Systems Interconnection) model facilitates network communication by providing a standardized framework that divides network communication into seven distinct layers. Each layer has specific functions and protocols that contribute to the overall process of transmitting data between devices.
By segmenting communication into these layers, the OSI model standardizes network functions, promoting interoperability and simplifying troubleshooting and development.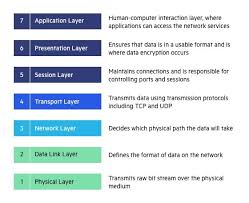
See lessHow does the OSI model facilitate network communication?
The OSI (Open Systems Interconnection) model facilitates network communication by providing a standardized framework that divides network communication into seven distinct layers. Each layer has specific functions and protocols that contribute to the overall process of transmitting data between deviRead more
The OSI (Open Systems Interconnection) model facilitates network communication by providing a standardized framework that divides network communication into seven distinct layers. Each layer has specific functions and protocols that contribute to the overall process of transmitting data between devices.
By segmenting communication into these layers, the OSI model standardizes network functions, promoting interoperability and simplifying troubleshooting and development.
See less