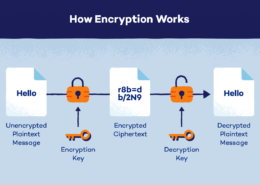
Encryption protects data by transforming it into an unreadable format using mathematical algorithms and keys. Here is a simplified process: Plaintext: The original, readable data that needs to be protected. Encryption Algorithm: A set of complex mathematical rules (e.g., AES, RSA) used to transformRead more
Encryption protects data by transforming it into an unreadable format using mathematical algorithms and keys. Here is a simplified process:
- Plaintext:
The original, readable data that needs to be protected.
- Encryption Algorithm:
A set of complex mathematical rules (e.g., AES, RSA) used to transform plaintext into ciphertext.
- Encryption Key:
A secret string of bits that the algorithm uses to encode the plaintext into ciphertext.
- Ciphertext:
The encrypted, unreadable data resulting from the encryption process.
Types of Encryptions:
- Symmetric Encryption:
– Uses the same key for both encryption and decryption.
– Requires both the sender and receiver to share the key secretly.
– Example: AES (Advanced Encryption Standard).
- Asymmetric Encryption:
– Uses a pair of keys: a public key for encryption and a private key for decryption.
– Enhances security by ensuring only the holder of the private key can decrypt the data.
– Example: RSA (Rivest-Shamir-Adleman).
Workflow:
- Encryption:
– The sender uses an encryption algorithm and key to convert plaintext into ciphertext.
- Decryption:
– The recipient uses the decryption algorithm and the correct key to revert ciphertext back to plaintext.
Use Cases:
- Protecting Stored Data:
- Securing Communication:
- Verifying Identities:
Encryption secures data by converting it into an unreadable format using mathematical algorithms and keys.
See less
Malware (malicious software) is designed to disrupt computer systems. It comes in many forms from suspicious downloads or emails, to tricking you into giving up personal information like passwords and credit cards. Malware can steal data, slow your computer’s performance by hogging resources, or canRead more
Malware (malicious software) is designed to disrupt computer systems. It comes in many forms from suspicious downloads or emails, to tricking you into giving up personal information like passwords and credit cards. Malware can steal data, slow your computer’s performance by hogging resources, or can even take complete control, allowing attackers to see your files or use your computer for their schemes. This can also spread like viruses, infecting your entire network and wreaking havoc on multiple devices. Using anti-malware software is crucial to protecting your system from these unwelcome guests.
See less